AWS IAM is at the heart of AWS security because it allows you to control access by creating users and groups, assigning specific permissions and policies to specific users, managing Root Access Keys, configuring MFA Multi-Factor authentication for added security, and much more. And, to top it all off, IAM is completely free to use!
The main purpose of IAM Users is that they can sign in to the AWS Management Console and can make requests to the AWS services.
The newly created IAM users have no password and no access key. If a user wants to use the AWS resources using the AWS Management Console, you need to create the user password. If a user wants to interact using the AWS programmatically (using the CLI (Command Line Interface)), you need to create the access key for that user. The credentials created for IAM User are what exactly uniquely identify themselves to AWS.
The security of the user's credentials can be enhanced by using the feature, i.e., Multi-Factor Authentication.
The newly created IAM Users do not have permissions, i.e., they are not authorized to access the AWS resources.
An advantage of using individual IAM Users is that you can assign the permissions individually. You can even assign the administrative permissions, who can administer your AWS resources and also administer other IAM Users.
Creating an IAM User (AWS Management Console)
o create a User using AWS Management Console:
Sign in to the AWS Management Console.
Open the IAM Console at https://console.aws.amazon.com/iam/home?region=us-east-2#/home.
On the navigation pane, click on the Users. After clicking on the Users.
Click on the Add User to add new users to your account. After clicking on the Add User.
Enter the User name for the user you want to create. You can create five users at a time.
Select the AWS access type. Either you want a user to have programmatic access, AWS Management Console access or both.
You can also give permission to the user to manage his or her security credentials.
How IAM Users Sign In To Your AWS Account
Open the link https://us-east-1.signin.aws.amazon.com/ to sign in to your AWS account.
An IAM User enters the user name and password assigned by you to login into the IAM Console.
Listing IAM Users
Sign in to the AWS Management Console by entering your email address and password.
Open the IAM Console.
In the navigation pane, click on the Users.
Listing all the Users in a Group
Sign in to the AWS Management Console by entering your email address and password.
Open the IAM Console.
In the navigation pane, click on the Group.
Delete an IAM User
Sign in to the AWS Management Console.
Open the IAM Console.
In the navigation pane, click Users.
Select the checkbox appears next to the user name.
From the User Actions list at the top of the page, select Delete User.
Click yes, Delete.
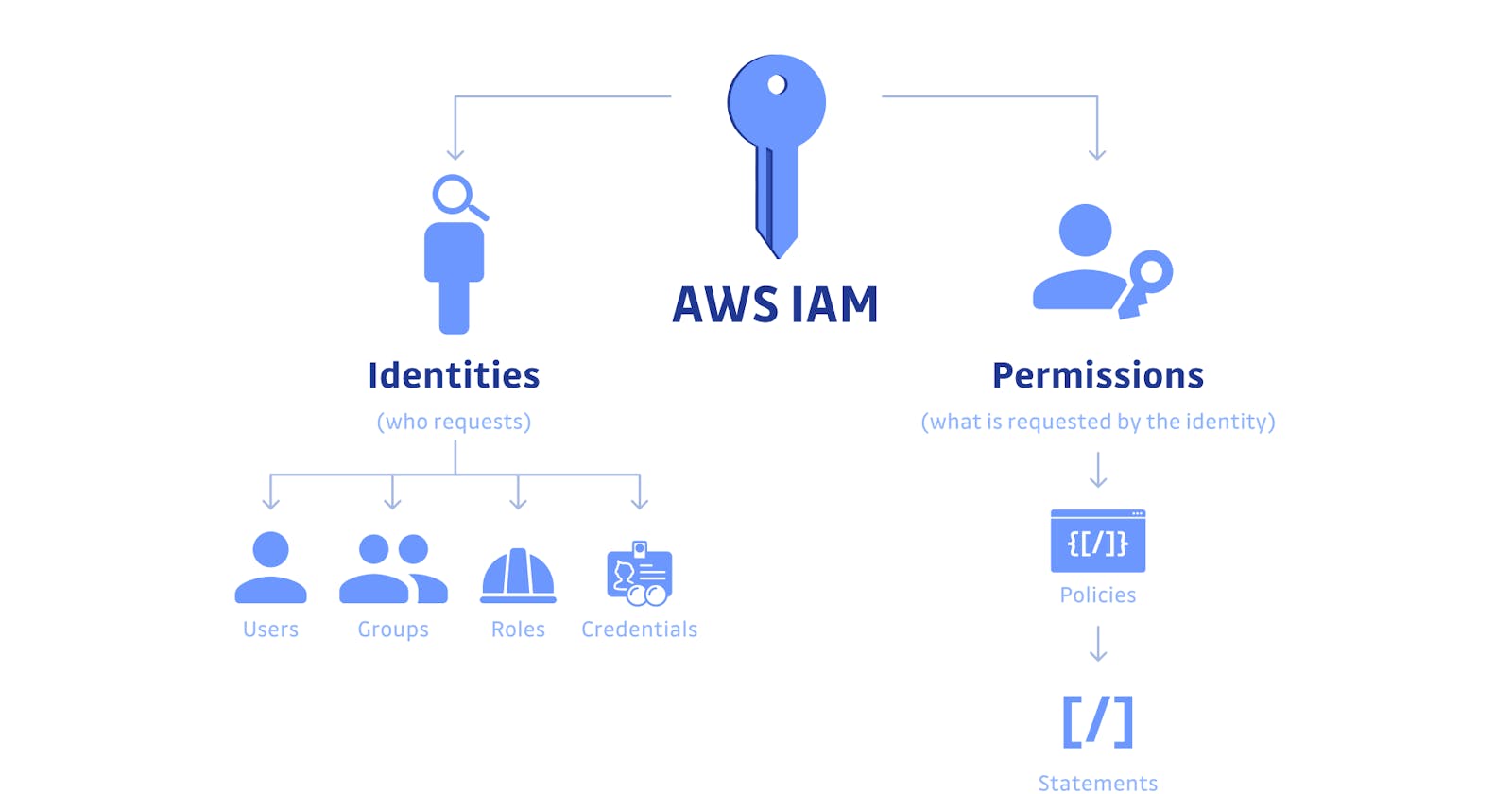
AWS IAM — Key Features
We should consider IAM to be the first step toward ensuring the security of all your AWS administrations and assets.
- Confirmation:
AWS IAM enables you to create and manage characters such as clients, groups, and jobs, allowing you to issue and enable verification for assets, individuals, administrations, and applications within your AWS account.
- Approval:
In IAM, access to executives or approval is comprised of two critical segments: Policies and Permissions.
Fine-grained consents:
Consider this: you need to give the business group in your organisation access to charging data, but you also need to give the engineering group full access to the EC2 administration and the marketing group access to specific S3 pails. You can design and tune these consents using IAM to meet the needs of your clients.
- Common admittance to AWS accounts:
Most organisations have multiple AWS accounts and must occasionally designate access between them. IAM allows you to do this without sharing your credentials, and AWS recently released ControlTower to further streamline multi-account designs.
- AWS Organizations:
You can use AWS Organizations to divide accounts into gatherings and assign consent limits for fine-grained control over multiple AWS accounts.
- Personality Federation:
In many cases, your organisation should combine access from other character providers, such as Okta, G Suite, or Active Directory. Identity Federation, a component of IAM, allows you to do this.
IAM policies
IAM Groups are a way to assign permissions to your organization's logical and functional units. IAM Groups are a tool to help with operational efficiency, bulk permissions management (scalable), and easy permission changes as individuals change teams (portable)
A group can have many users, and a user can be a member of multiple groups.
Groups cannot be nested; they can only contain users and not other groups.
IAM Roles
An IAM role, like a user, is an AWS identity with permission policies governing what the identity can and cannot do in AWS
For specific access to services, you can authorize roles to be assumed by humans, Amazon EC2 instances, custom code, or other AWS services.
Roles do not have standard long-term credentials associated with them, such as a password or access keys; rather, when you assume a role, it provides you with temporary security credentials for your role session.
AWS IAM Access Analyzer
Do yourself a favour and start using the IAM access analyzer for organizational security if you have two or more AWS accounts. The access analyzer displays all AWS resources that are accessible outside of your AWS organization.
IAM Access Analyzer continuously monitors resource policies for changes, removing the need for infrequent manual checks to catch issues as policies are added or updated.
It enables you to create a comprehensive report for all of your AWS assets that can be accessed publicly by utilizing Access Analyzer.
Access Analyzer is a component of Amazon's Provable Security endeavour to achieve the highest levels of security utilizing mechanized reasoning innovation and scientific reasoning.
THANK YOU!